ESD Alliance and SEMI Take on Software Piracy
December 5th, 2023 by Paul Cohen

Note: This article originally appeared in the November/December issue of DENA (Designing Electronics North America).
In September 2023, SEMI announced plans to begin licensing its server certification protocol, an industry-developed solution to combat software piracy, which is a growing and costly concern for software vendors and their users.
This three-year project was managed by the Electronic System Design Alliance (ESD Alliance), a SEMI Technology Community, with Cadence Design Systems, Siemens EDA, and Synopsys participating in the development effort to provide strong protection against piracy. The protocol was reviewed and approved by an independent group of semiconductor companies that rely on EDA tools in their business operations, thereby giving it a user seal of approval.
Unauthorized use of licensed software—more commonly known as software piracy—is a problem that impacts both providers and users of licensed software. Industry reports estimate unauthorized access to software costs the industry billions of dollars annually.
The Software Alliance—the leading advocate for the global software industry whose members create software solutions that help businesses modernize and grow—estimates that unlicensed and counterfeit software costs companies nearly $359 billion per year. Of course, unauthorized compliance covers a range of piracy, from malware and ransomware to other critical security threats. Unlicensed software is estimated to cost companies nearly $46 billion a year in revenue.
A growing concern
Piracy is a growing concern for all software providers. Unauthorized use deprives them of revenue needed to continue to enhance their products and develop new software tools required by the end users for their product development. It also puts the legitimate end users of the tools at a disadvantage, as they will be competing in the marketplace against companies that did not make a similar investment in the same software.
Many high value software applications such as engineering design software rely on a license manager to authorize the use of the software per the license agreement with the software vendor. Such agreements often include the number of simultaneous users for each software product. For each use, the application contacts the license server software to determine if a license is currently available and, if so, allows the software to run. Previous license manager solutions used specific information derived from the physical machine hosting the license server software (often the MAC address) to prevent unauthorized use. However, that identifier can easily be duplicated or cloned, allowing activation of multiple unauthorized servers, which can then allow additional, unauthorized copies of the application software to be used.
Virtualization adds to the problem
The current trend toward virtualization technologies can make license server identifiers even easier to clone. Even where the physical machine information is available to the virtual host (which is not always the case), multiple virtual machines may share the same physical host, thus allowing multiple license server instances to have the same identifier. The protocol addresses this concern by uniquely identifying each customer license server, regardless of whether it is physical or virtual.
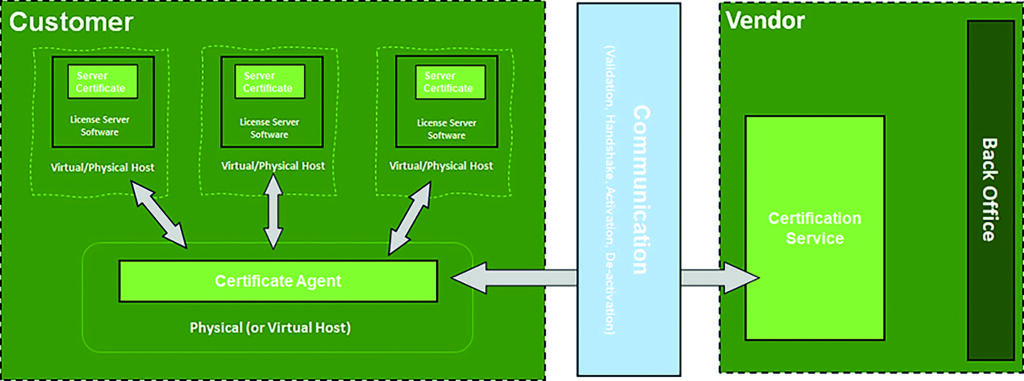
Locked and floating certificates
To address the trend toward virtual hosts, the SEMI server certification protocol includes two types of certification certificates. First is a locked certificate, which can only be used on a specific host. This is like the previous methodology which relied on a specific license server host machine. With the recent trend towards virtualization, the protocol development team added a floating certificate, which can be used on many hosts, and which includes a methodology to assure only one authorized server is active at a time.
The locked certificate is similar to the current license server methodology in that it requires a machine specific identifier, or “fingerprint.” This fingerprint is based on a variety of machine characteristics, sufficient to make each fingerprint unique and difficult to reproduce (clone). The machine data collected is not proprietary, and the details are included in the protocol specification. As part of the protocol review, major design software customers have reviewed and approved the fingerprint contents.
The floating certificate cannot rely on a specific machine fingerprint, since there may not be a specific machine hosting the license server. Thus, the floating version of the protocol relies on a handshake with the vendor to assure only one instance of an authorized server is active at any given time.
Addressing customer concerns
It is common for larger design companies to employ multiple license servers which may be in different geographic locations. The protocol does continue to support multiple, authorized license servers.
A key concern of semiconductor companies is the high availability of license servers since machines can and do occasionally fail or need to be updated. While the protocol addresses unauthorized use, it also supports the use of authorized backup license servers.
Another concern of software customers is the actual usage of the licensed software applications, as this information could affect future negotiations between the vendor and customer. It is important to note that the protocol only authorizes the license server software to issue usage licenses and does not track which software licenses are subsequently used. Thus, no information about actual software use is included in the handshake.
It is also important to note that while the protocol was developed by companies in the electronic design automation (EDA industry), it is not industry specific and can be employed for use with any license management system for high-value software products. The protocol simply provides the ability to uniquely identify each customer license server, independent of the licensed software itself.
Credit where credit’s due
Much of the credit for the protocol development effort goes to the ESD Alliance’s License Management/Anti-Piracy (LMA) Committee. This highlights how an industry organization like SEMI has the ability to gather industry players to work together to solve critical problems.
New solutions such as this will enable other segments of the software industry to combat piracy, providing a secure license infrastructure compatible with diverse tool environments. Deployment of this capability will increase confidence that all licenses used are fairly acquired, making it harder for unethical players to gain competitive advantage through the theft of licenses, and allowing software suppliers to continue to develop innovative products.
semi.org/en/communities/esda
Related
This entry was posted
on Tuesday, December 5th, 2023 at 3:52 pm.
You can follow any responses to this entry through the RSS 2.0 feed.
You can leave a response, or trackback from your own site.